PagelShield
Courses
Enhance your secure development lifecycle proactive with trained personnel to save costs in findings bug too late in the lifecycle.
Trainings
The contents of the trainings are determined individually for your organization. Trainings are characterized by the fact that they are strongly guided by slides and related hands-on tasks.

Web-Security Training Advanced
Train developers web threats and how to develop secure code.

Container Security
Conduction of a container security workshop to show the threats by operating containers.

Open Policy Agent
Open Policy Agent Description The Open Policy Agent (OPA) is an open source and generic engine that can be used to enforce uniform and context-aware

Security Awareness Training
DevSecOps Workshop Übersicht Using the DevSecOps Maturity Model (dsomm.timo-pagel.de), designed by the speaker, different dimensions of security in DevOps are explained. The content will be
Secure Modern Development
Durchführung einer strukturierten Analyse zur Identifizierung von Bedrohungen in IT-Systemen.
Workshops
Compared to trainings, workshops are even more adapted to your needs, so that concrete existing methods and technologies are jointly understood in order to identify optimization potential.
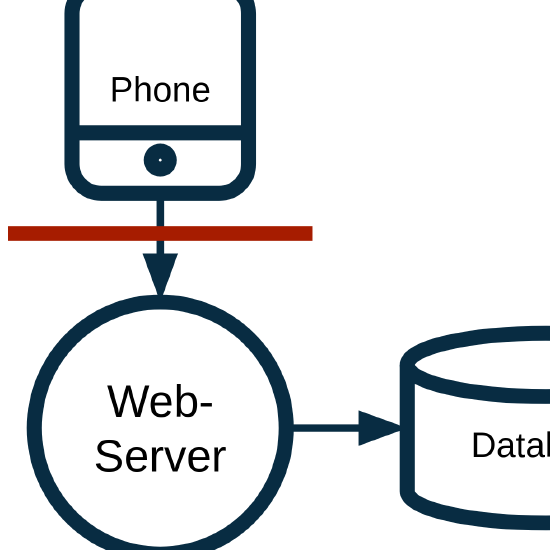
Agile Security
Security in the agile software development cycle Description The training will demonstrate how security can be integrated into modern agile development. Train efficiently Content Presentation
Agile Threat Modeling
Conduction of a structured analysis to identify threats in IT systems.

DevSecOps Workshop
DevSecOps Workshop Description Using the DevSecOps Maturity Model (dsomm.timo-pagel.de), designed by the speaker, different dimensions of security in DevOps are explained. The content will be
Assessment
As part of an assessment, a scope is first defined and then the current status and the target status are analyzed. This can be done on a strategic, process-related or technical level.

Cloud Security Strategy
Assessment of the cloud security strategy or the implementation. Giving recommendations to enhance cloud security.

Security Assessment and Management
Assessment of the overall security status, planning of activities and check of the effectiveness.

DevSecOps-Assessment
Assessment of the current DevOps security status, planning of activities and check of the effectiveness.
Security Check
Quick security check of web applications to identify threats in running applications for common pit falls.

WordPress Security
WordPress is the most popular blog system on the market today. Attackers know this too, which is why more and more automated attacks are being run against WordPress. This workshop will show you what attacks exist and what countermeasures you can take.

Training Methodology and Options
Academic-level content
Training material is based on up to date content.
Customizable curriculum
The agenda is customizable so that it fits your culture and used technology.
On-site or remote
Trainings are held according to your preference remote or On-site.